One Laptop Manufacturer Had To Stop Janet Jackson Crashing Laptops

There are all manner of musical myths, covering tones and melodies that have effects ranging from the profound to the supernatural. The Pied Piper, for example, or the infamous “brown note.”
But what about a song that could crash your laptop just by playing it? Even better, a song that could crash nearby laptops in the vicinity, too? It’s not magic, and it’s not a trick—it was just a punchy pop song that Janet Jackson wrote back in 1989.
Rhythm Nation
As told by Microsoft’s Raymond Chen, the story begins in the early 2000s during the Windows XP era. Engineers at a certain OEM laptop manufacturer noticed something peculiar. Playing Janet Jackson’s song Rhythm Nation through laptop speakers would cause the machines to crash. Even more bizarrely, the song could crash nearby laptops that weren’t even playing the track themselves, and the effect was noted across laptops of multiple manufacturers.
Rhythm Nation was a popular song from Jackson’s catalog, but nothing about it immediately stands out as a laptop killer.
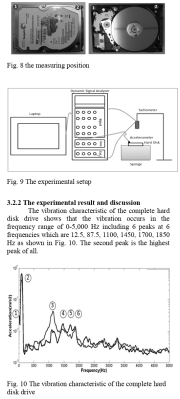
After extensive testing and process of elimination, the culprit was identified as the audio frequencies within the song itself. It came down to the hardware of the early 2000s laptops in question. These machines relied on good old mechanical hard drives. Specifically, they used 2.5-inch 5,400 RPM drives with spinning platters, magnetic heads, and actuator arms.

Unlike today’s solid-state drives, these components were particularly susceptible to physical vibration. Investigation determined that something in Rhythm Nation was hitting a resonant frequency of some component of the drive. When this occurred, the drive would be disturbed enough that read errors would stack up to the point where it would trigger a crash in the operating system. The problem wasn’t bad enough to crash the actual hard drive head into the platters themselves, which would have created major data loss. It was just bad enough to disrupt the hard drive’s ability to read properly, to the point where it could trigger a crash in the operating system.
There was a simple workaround for this problem, that was either ingenious or egregious depending on your point of view. Allegedly, the OEM simply whipped up a notch filter for the audio subsystem to remove the offending frequencies. The filter apparently remained in place from the then-contemporary Windows XP up until at least Windows 7. At this point, Microsoft created a new rule for “Audio Processing Objects” (APO) which included things like the special notch filter. The rule stated that all of these filters must be able to be switched off if so desired by the user. However, the story goes that the manufacturer gained a special exception for some time to leave their filter APO on at all times, to prevent users disabling it and then despairing when their laptops suddenly started crashing unexpectedly during Janet Jackson playlists.
As for what made Rhythm Nation special? YouTuber Adam Neely investigated, and came up with a compelling theory. Having read a research paper on the vibrational behavior of a 2.5-inch 5,400 RPM laptop hard disk, he found that it reported the drive to have its largest vibrational peak at approximately 87.5 Hz. Meanwhile, he also found that Rhythm Nation had a great deal of energy at 84.2 Hz. Apparently, the recording had been sped up a touch after the recording process, pushing the usual low E at 82 Hz up slightly higher. The theory being that the mild uptuning in Rhythm Nation pushed parts of the song close enough to the resonant frequency of some of the hard drive’s components to give them a good old shaking, causing the read errors and eventual crashes.
It’s an interesting confluence of unintended consequences. A singular pop song from 1989 ended up crashing laptops over a decade later, leading to the implementation of an obscure and little-known audio filter. The story still has holes—nobody has ever come forward to state officially which OEM was involved, and which precise laptops and hard drives suffered this problem. That stymies hopes for further research and recreation of this peculiarity. Nevertheless, it’s a fun tech tale from the days when computers were ever so slightly more mechanical than they are today.